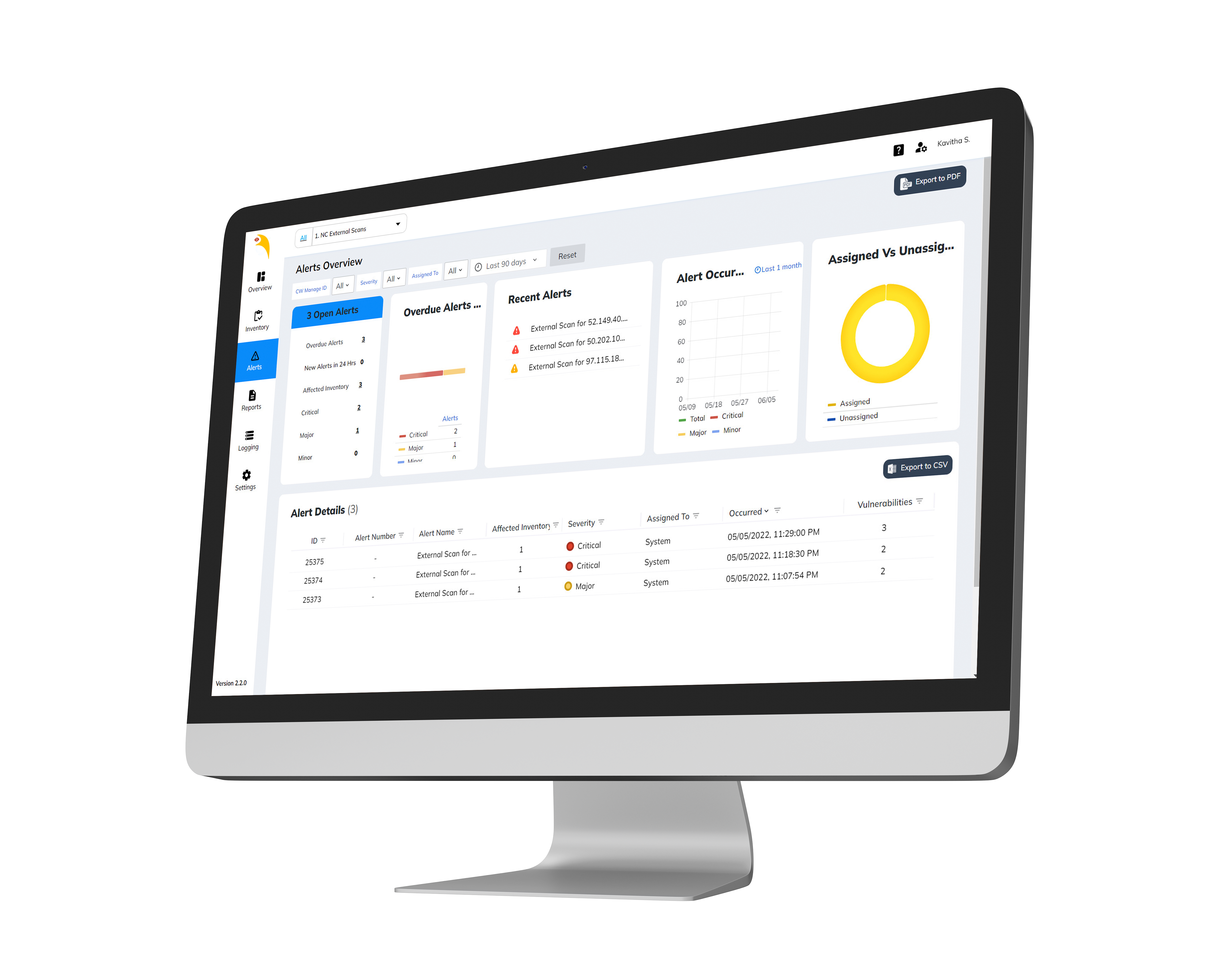

What is Beak Vulnerability Module?
Developed by experts with the utmost focus on customer data and platform security, our vulnerability module is designed to protect your business and reputation against any potential damages. Our lightweight agents' scan, evaluate, and prioritize the vulnerabilities on your network in real-time to ensure business continuity.
Key features include:
- Agent & Agentless monitoring Platform
- Automated asset discovery and onboarding
- Unified portal to bring together on-premise and Cloud Infrastructure
- Real-time asset monitoring and scanning for security threats
- Intelligent Alerts powered by AI to avoid false alarms
- Highly configurable and scalable with distributed deployment
- Deep Insights on Devices & Applications with powerful dashboards
- Monitors growing Docker containers and Kubernetes based platforms
- AI-powered remediations for faster turnaround time
- Interactive dashboards for organization-wide visibility


How does Beak work for your business?
It provides a unified view of your digital assets, detects & maps vulnerabilities and classifies & prioritizes them for remediation. Moreover, you can track your vulnerability remediation SLA's through dashboards and reports and remain compliant.
Your Security is our Top Priority! Know what set’s up apart.
Vendor Comparison – Vulnerability & Remediation
| Nessus | Qualys | Beak | |
|---|---|---|---|
| Software Inventory | *** | **** | **** |
| Vulnerability Identification & Prioritization | *** | **** | **** |
| Integration | *** | **** | **** |
| Reporting, Analysis, and Metrics | *** | *** | **** |
| Enterprise Solution | * | **** | **** |
| Ease of Deploy | ** | ** | **** |
| Ease of Use | * | ** | **** |
| Pricing & Support | ** | * | **** |

Comparison - CyberCNS vs Beak Vulnerability Engine
| Cyber CNS | Beak |
|---|---|
| Offline Vulnerability detection | Real-time Scan |
| Product based detection | Package based detection |
| More false positives | Minimal false positives |
| No hardware/drivers scanning | Vulnerabilities on drivers/hardware are detected |
| Not possible to accept risk | Custom selection for accepting risk |
| No remediation engine | Fully automated remediation engine |
| No vulnerability categorization option | Custom vulnerability classification |
| Detects port vulnerabilities using LW agent | Detects port vulnerabilities only using Probe scanner |
Why compromise on infrastructure security?
Lets Connect
Home | About Us | Privacy Policy | Contact
Copyright © 2022 iLink Digital, Inc.
All Rights Reserved


